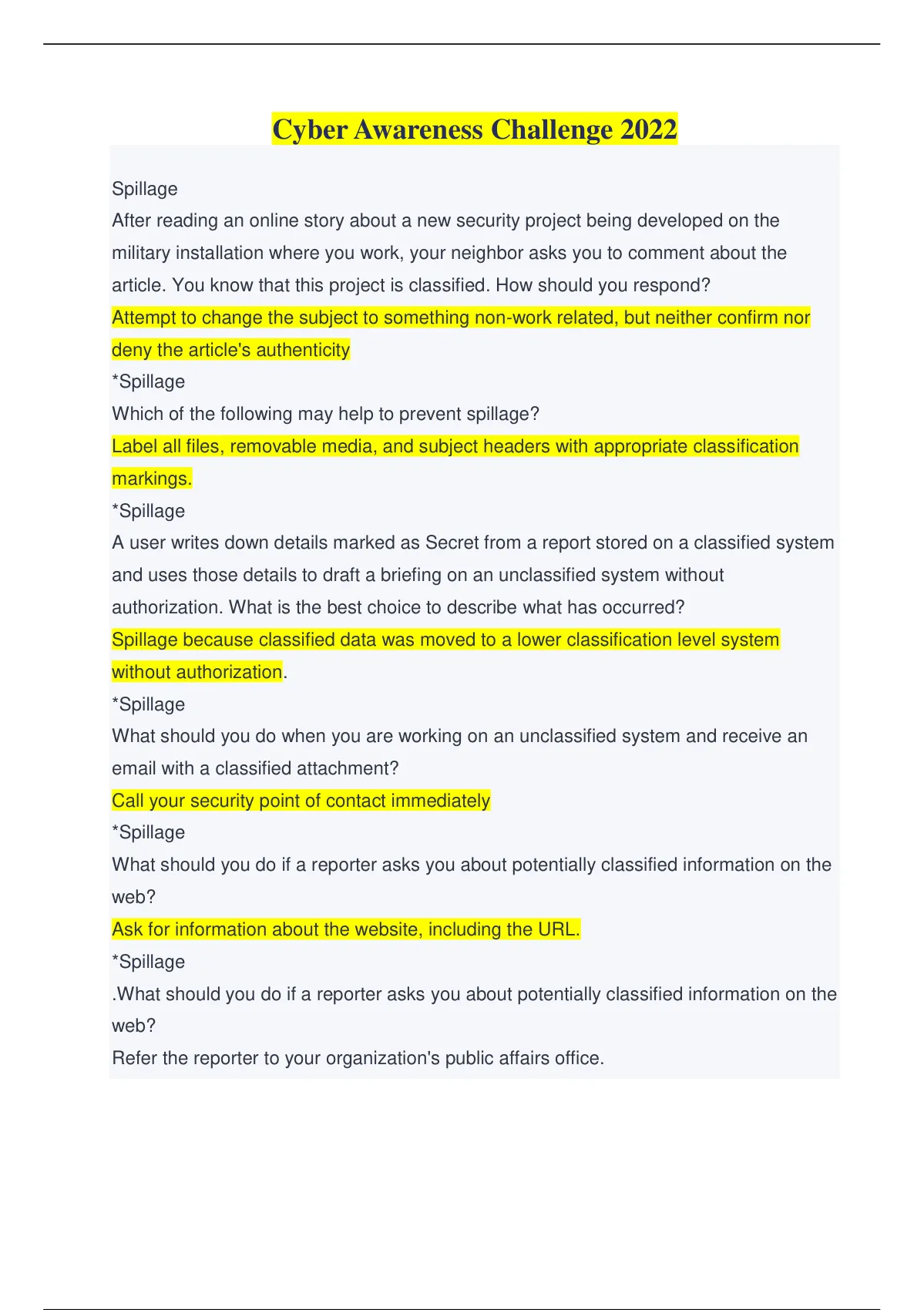
Jko Cyber Awareness Challenge Answers 2025. It appears that your browser configuration may not meet all of the requirements to run this courseware for the following reason s: Press the f12 key to open up the developer tools for internet explorer.
Cyber awareness challenge 2025 knowledge check answers contents hide 1 cyber awareness challenge 2025 knowledge check answers 2 standard challenge answers. Which of the following is true of compressed urls (e.g., tinyurl, goo.gl)?
Dod Cyber Awareness Challenge 2025 Jko Rahel Carmelle, Which of the following is true of compressed urls (e.g., tinyurl, goo.gl)?

Cyber Awareness Challenge 2025 Knowledge Test Pdf Download Kaela Maridel, The cyber awareness challenge aims to shape user behavior by highlighting actionable steps authorized users can take to reduce risks and fortify the.

Jko Dod Cyber Awareness Challenge 2025 Delia Fanchon, Once you have the cyber awareness challenge open and on the task list section.

Jko Cyber Awareness Challenge 2025 Quizlet Maddi Tabbatha, The purpose of the cyber awareness challenge is to influence behavior, focusing on actions that authorized users can engage to mitigate threats and vulnerabilities to dod information.

Dod Cyber Awareness Challenge 2025 Quizlet Nelly Yevette, Encrypting data stored on removable media.
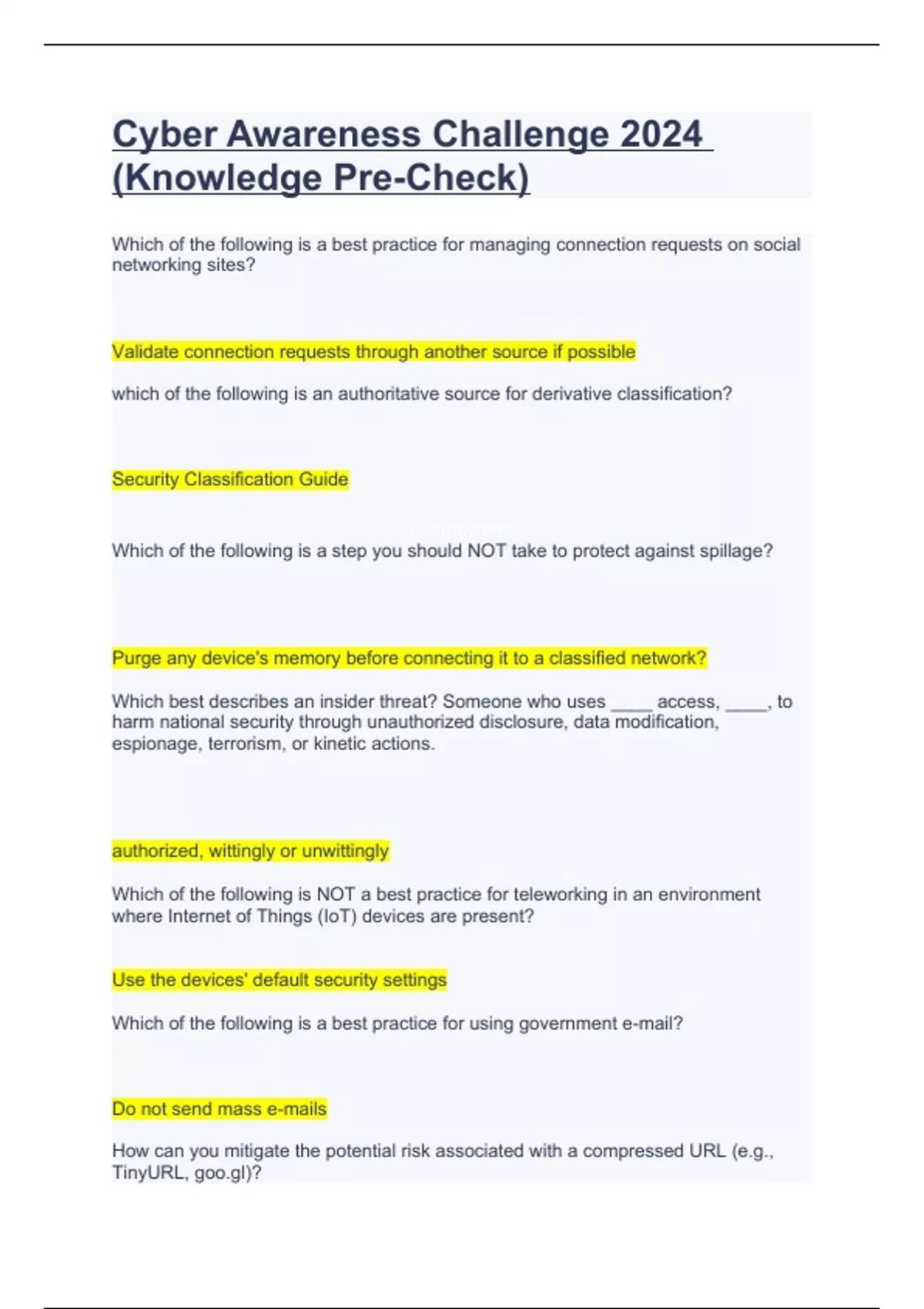
Dod Cyber Awareness Challenge 2025 Legra Natalee, Which of the following is true of sensitive compartmented information facilities (scifs)?

Jko Cyber Awareness 2025 Answers Ronny Auguste, What conditions are necessary to be granted access to sensitive compartmented information (sci)?

Cyber Awareness Challenge 2025 Test Answers Github Elise Helenka, Sci is a program that _____ various types of classified information for _____ protection and dissemination or distribution control.

CYBER AWARENESS CHALLENGE EXAM 2025/DOD CYBER AWARENESS CHALLENGE 2025, Once you have the cyber awareness challenge open and on the task list section.

Cyber Awareness Challenge 2025 Pretest Leah Lorinda, The purpose of the cyber awareness challenge is to influence behavior, focusing on actions that authorized users can engage to mitigate threats and vulnerabilities to dod information.